Although 2020 will surely go down as 'virus year,' viruses on Mac are not going anywhere. Just recently, a fake Adobe Flash Player updater named Shlayer has infected 10% of all Macs in the world (according to Kaspersky's lab).
Even newer malware type, Tarmac, is increasingly sweeping the Mac world. All it takes to contract it is to open a pirated website or even click a link on Wikipedia. At least that's been the case with Shlayer, which had its malicious links planted inside Wikipedia's external resources.
How to remove a virus from an iPhone or iPad. IOS malware is rare but not unknown. Here's how to detect - and safely get rid of - viruses on your iPhone or iPad. The Apple logo will appear; at. Mac Malware Remover for Mac is a simple program that effectively scans for a few known Mac viruses, but lacks the features of a full security program. The program download completed as quickly as. Nov 14, 2017 Anyone can manually initiate a scan and remove malware with Malwarebytes for Mac without spending a penny. The Malwarebytes Premium features that will monitor your Mac for malware and spyware, prevent infections before they occur, and automatically download updates do cost money, but Malwarebytes does provide a 30-day free trial.
Apple Support Malware Removal Tool
In this Mac Malware removal guide, we'll tell you how to get rid of malware on your Mac. We'll also cover how to tell apart different viruses on Mac: adware, scareware, and others. We'll be using the manual methods as well as some respected antivirus tools for Mac. Let's go.
What is malware
First off, let's point out that the term 'malware' is a broad term for all unwanted intrusions. It's also not synonymous with the term 'virus' because the latter is only a model of distribution i.e. how an app self-replicates. Here are common types of malware you can encounter on Mac:
- Download managers — download unauthorized objects
- Spyware and keyloggers — steal users' personal data
- Backdoor infections — apps that remotely seize control of your computer
- Rootkit — infiltrate admin privileges
- Botnet — turn your Mac into a shadow bot
- Trojan horses — apps disguised as legit software
- Ransomware — lock your Mac's screen
- PUP — potentially unwanted programs
Among these, PUPs are the most numerous type. According to Malwarebytes, Windows platform is no longer a hotbed for viruses — the macOS is. The has been a 400% spike in macOS-specific malware infections with an average of 11 threats per number of Mac devices — the same figure for Windows is only 5.8.
Mac malware: The symptoms
Oftentimes a malware app would trick you into believing it's perfectly harmless. Such apps are known to disguise themselves as antiviruses, extractors or video players. But how to check your Mac for viruses? Here are some of the tell-tale signs:
- A sudden drop in Mac's performance or frequent freeze-ups.
- Pages that you visit get obscured with ads.
- Unexpected Mac reboots or apps starting for no reason.
- Your browser installs suspicious updates automatically.
How Mac can get infected with malware
By clicking on fake Flash Player updater. Or by installing a seemingly useful browser extension. As of 2020, a trojan browser extension NewTab infected 30 million Mac computers. This malware disguised itself as a parcel tracking helper but was in fact spreading ads. So how to protect your Mac from malware? You can start by studying typical infection gateways.
How to remove a virus from Mac
Just as with any disease, to doctor a virus you need to remove the infected part of your software — as simple as that.
1.Remove malware from Mac manually:
The Activity Monitor
If you know which app on your Mac is malicious, you're half-way through the problem. First of all, you need to close the app and then root it out from the system processes.
- Open Activity Monitor (type its name in the Launchpad).
- Locate the problematic app in the Processes.
- Use [x] button to quit the process
Now go back to your Applications and move the app to the Trash bin. Immediately empty the Trash.
This method is simple, but for the best malware removal results, you'd have to invest a bit more time. There are still parts and pieces of the virus app scattered around your system folders. It's a bit like killing a dragon that re-grows its head after you've chopped it off. To remove malware from your Mac completely, it's better to use a powerful uninstaller.
Do a quick search for virus-infected .DMG files within your Downloads. The potential culprits could be recently downloaded files, especially media-related ones. Delete them and empty the Trash bin.
2. Get rid of malware using CleanMyMac X
CleanMyMac X has a 10-year reputation of guarding Macs around the world. The app will scan your Mac for any vulnerabilities and offer immediate removal if it finds something suspicious. CleanMyMac detects thousands of malware threats, including viruses, adware, spyware, ransomware, cryptocurrency miners, and more. The app's database is regularly updated to keep all those '-wares' away from your Mac.
Here's how to remove malware from your Mac:
- Download CleanMyMac X — it's free to download.
- Click Malware Removal tab.
- Click Scan.
- Click Remove.
- Done!
3. Remove Mac malware from your Login Items
Most adware or spyware will try to sneak inside the bootup process. Good news, you don't have to be Kaspersky to prevent this.
- Go to the Apple menu > System Preferences.
- Choose Users & Groups section.
- Make sure if your username is highlighted.
- Open Login Items tab.
Now use the '—' sign to disable all the suspicious apps (like Mac Defenders) that you'll find. Restart your Mac for the changes to take place.
4. Get rid of pop-up ads on Mac
Advertising pop-ups are browser-related, so whatever browser you are using, be prepared for a thorough cleanup. First off, don't buy into whatever the ad is telling you. Some scary alerts would mention 343 viruses found on your Mac forcing you to immediately install a 'Mac Defender' or 'Mac Security' tool. Just ignore it and don't click anywhere on the pop-up. Use [x] button and if it doesn't close the ad, Ctrl + click the browser icon to quit the browser completely.
Hold the Shift key when starting a new Safari session. This way all your previous tabs (including the ad pop-up) will not be reopened.
How to block pop-up ads in Safari
- Open Safari preferences (in the top menu).
- Go to the Security tab.
- Tick 'Block pop-up windows'.
How to get rid of pop-ups in Chrome
- Open Chrome Settings (a three-dot icon)
- Click Privacy and security
- Go to Site settings > Pop-ups and redirects
- Locate the Popups tab and block them from appearing
Additionally, make sure your browser's homepage is set to standard Google page or other trusted source.
5. Clean up extensions to remove adware from Mac
Apple lists several browser extensions as potentially malicious. The list includes:
- Amazon Shopping Assistant by Spigot Inc.
- Slick Savings by Spigot Inc.
- FlashMall
- Cinema-Plus
This is just to give you an idea of how different these adware extensions could be. But if you're looking at how to remove malware from the Mac Safari browser, follow this path.
Remove extensions in Safari
- Go to Safari Preferences
- Choose the Extensions tab
- Select an extension and click Uninstall
Disable browser extensions in Chrome
And here's how to remove malware from Mac Chrome. Open Chrome and click Window in the top menu. In the bottom of the list choose Extensions. This opens up the list of all your installed extensions. Now use a trash bin icon to remove the ones you suspect are adware viruses. Right after that, your Chrome experience should get much less distracting.
Just to be doubly sure, we recommend you to remove all the extensions you'll find. Later you can re-install each one separately.
TIP: How to remove Mac adware via Javascript
You can prevent some malware attacks from happening by disabling JavaScript in your browser. Although, it may break certain webpages, your browsing will get more secure and, likely, faster too.
To disable JavaScript in Safari
- Go to Safari Preferences > Security.
- Uncheck Enable JavaSript.
6. Launch Agents and Daemons: Where else to look
So far we've covered browser Extensions, Applications, and Login Items trying to remove malware from your Mac. But these are not the only locations where malicious agents may be hiding. Another type of system services that could be affected by malware are the so-called Launch Agents and Daemons — yes, the name does derive from the word demon. These are small helper programs that stealthily run in the background, like software updaters or automatic backups.
While Launch Agents and Daemons are two different entities, both can be infiltrated by malware. As it often happens, trojan apps would place their executable files within the Launch Agents folder. The result — the virus app launches automatically and potentially harms or steals your data.
7.How to remove daemons and agents from Mac startup
- Click Finder.
- Choose Go > Go to Folder.
- Type in:
/Library/LaunchDaemons
For Launch Agents, repeat the steps above, but this time search in 2 more locations:
/Library/LaunchAgents
~/Library/LaunchAgents
Inside you'll find a bunch of PLIST files and if some of them look suspicious to you, delete them. Sure, the names of these files may not be very telling, but if you already know the problematic app that you are after, knowing this folder may help you fully extinguish it.
Don't forget to reboot your Mac — until you do, all these files are still in memory.
One more way to remove daemons, agents, and plug-ins
If the manual path described here sounds too complicated, you can again be rescued by CleanMyMac X. This app has a special tool to remove malware Launch Agents.
- Download CleanMyMac X (it's free to download).
- Install the app.
- Click Optimization tab > Launch Agents
- Click Perform.
By the way, this app has a real-time anti-malware monitor. It monitors for any problematic apps that try to get into your Launch Agents. If it finds such, it will notify you and offer to remove the intruder.
If all else fails
Below a few more ideas to help you remove malware from Mac.
- Switch to a different user account and do a full system cleanup.
- Restore your Mac using Time Machine (to the point before it got infected).
- Update all your software, including the macOS.
How to protect Mac from malware
As a conclusion, we've prepared a few basic tips to minimize your chance of catching malware in 2020 and beyond. They are just as relatable for a PC computer.
- Closely read those dialogue boxes
- Get a reliable password manager app
- Browse anonymously
- Cover your webcam when possible
- Use passphrases instead of passwords
- Create an 'emergency' bootable SD card for your Mac
OK, looks we've covered how to remove malware from Mac including both manual and software solutions. Hope your Mac stays virus-free and may you never click on those scary Mac alerts again.
These might also interest you:
DON'T PANIC! But be aware that the Internet is riddled with potential threats to the security and well-being of your Mac or iOS device. No computer system is completely immune from possible attack, but Apple's OS X (being Unix-based) is less vulnerable than most, particularly the latest versions from Lion onwards. The following seeks to offer some guidance on the main security threats and how to avoid them. If you have further questions please post in the forum appropriate to your particular hardware or operating system.
There are many forms of ‘Malware' that can affect a computer system, of which ‘a virus' is but one type, ‘trojans' another. Using the strict definition of a computer virus, no viruses that can attack OS X have so far been detected 'in the wild', i.e. in anything other than laboratory conditions. The same is not true of other forms of malware, such as Trojans. (The expression ‘malware' is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software. Not all malware are viruses.) Whilst it is a fairly safe bet that your Mac will NOT be infected by a virus, it may have other security-related problem, but more likely a technical problem unrelated to any malware threat.
Since the introduction of Snow Leopard, Apple OS X has an anti-malware system built-in known as XProtect but officially called File Quarantine (see here: http://support.apple.com/kb/HT3662 ), which may alert you to, and prevent installation of, certain forms of malware. Later versions of OS X include further features to protect you, about which here: http://support.apple.com/kb/PH11432 and Apple also recommend that you take simple steps to protect your Mac as detailed here: http://support.apple.com/kb/PH10580
So what other anti-virus software do I need (or if I am still running Tiger or Leopard) ?
Mac virus clean up. Whilst viruses designed to attack the Microsoft Windows operating system cannot affect Apple OS X, it is possible to pass on a Windows virus, which you may have received but not noticed, to a Windows user, for example through an email attachment. Many use the free ClamXav just to check incoming emails for this reason. Our resident expert Thomas A Reed offers excellent guidance on this subject here: www.thesafemac.com/mmg
Do not install Norton Anti-Virus on a Mac as it can seriously damage your operating system. Norton Anti-Virus is not compatible with Apple OS X.
Do not install MacKeeper or iAnti-Virus: See this User Tip: https://discussions.apple.com/docs/DOC-3022
FAKE ANTI-VIRUS SOFTWARE and associated MALWARE (To repeat: the expression ‘malware' is a general term used by computer professionals to mean a variety of forms of hostile, intrusive, or annoying software.)
Do not be tricked by 'scareware', such as pop-ups on your browser, that tempts computer users to download fake anti-virus software that may itself be malware.
Once installed, the software may steal data or force people to make a payment to register the fake product. Examples include MacKeeper and iAntivirus, but there are others. Also, beware of MacSweeper and MACDefender* (also goes under the name of MacProtector, MacGuard, MacSecurity or MacShield): These are malware that mislead users by exaggerating reports about spyware, adware or viruses on their computer in an attempt to obtain payment for an application that does nothing that free utilities do not also offer, and in many cases will also mess up your system.
*Malicious software dubbed MACDefender takes aim at users of the Mac OS X operating system by automatically downloading a file through JavaScript. But users must also agree to install the software, leaving the potential threat limited.
*(This malware is not to be confused with MacDefender, the maker of geocaching software including GCStatistic and DTmatrix. The company noted on its site it is not affiliated with the malware.)
Malware spreads through search engines like Google via a method known as 'SEO poisoning.' The sites are designed to game search engine algorithms and show up when users search for certain topics. It is always a good idea to Block Pop-ups in your browser preferences.
TROJANS and RE-DIRECTION TO FAKE WEBSITES
The appearance of Trojans and other malware that can possibly infect a Mac seems to be growing, but is a completely different issue to viruses.
If you allow a Trojan to be installed, the user's DNS records can be modified, redirecting incoming internet traffic through the attacker's servers, where it can be hijacked and injected with malicious websites and pornographic advertisements. The trojan also installs a watchdog process that ensures the victim's (that's you!) DNS records stay modified on a minute-by-minute basis.
Mac users should always obtain their copy of Adobe Flash Player directly from Adobe's official website Macbook pro 10 11. and to disable the 'Open 'safe' files after downloading' option in Safari Preferences/General to avoid automatically running files downloaded from the Internet. Also, do not turn on Java in Safari Preferences/Security. Few websites use Java. Javascript is something entirely different and should be left active.
(Adobe is aware of malware posing as its Flash Player and warns users to ignore any updates that didn't originate on its own servers. 'Do not download Flash Player from a site other than adobe.com,' said David Lenoe, Adobe's product security program manager, in an entry on Adobe Product Security Incident Response Team's PSIRT blog. 'This goes for any piece of software (Reader, Windows Media Player, QuickTime, etc). If you get a notice to update, it's a good idea to go directly to the site of the software vendor and download the update directly from the source. If the download is from an unfamiliar URL or an IP address, you should be suspicious.')
Last, but by no means least, using Open DNS is the simplest way of preventing infection in the first place. Open DNS also protects against phishing attacks, re-directs, speeds up your internet connection - see below.
How to get it:
Java can present serious security threats: Users with Intel Macs running Snow Leopard OS 10.6 or later versions of OS X should ensure that they have downloaded and installed all the recent Java updates from Apple, which are designed to prevent infection and also remove any infection already present.
From the introduction of Lion onwards, new Macs do not have either Flash Player nor Java installed.
+++ OTHER ISSUES +++
Apple Malware Removal For Macbook Air
HOW TO AVOID RE-DIRECTION
Adding Open DNS codes to your Network Preferences should give good results in terms of added security (phishing attacks, re-direction etc) as well as speed-up of your internet connection:
Open System Preferences/Network. Double click on your connection type, or select it in the drop-down menu, and in the box marked 'DNS Servers' add the following two numbers: Dropdmg 3 3 download free.
208.67.222.222
208.67.220.220
(You can also enter them if you click on Advanced and then DNS)
Sometimes reversing the order of the DNS numbers can be beneficial in cases where there is a long delay before web pages start to load, and then suddenly load at normal speed:
There may be other ways of guarding against Trojans, viruses and general malware affecting the Mac, and alternatives will probably appear in the future. In the meantime the advice is: be careful where you go on the web and what you download!
GENERAL ADVICE ON HOW TO AVOID INFECTION IN THE FIRST PLACE:
1. Avoid going to suspect and untrusted Web sites, especially p'orn'ography sites.
2. Check out what you are downloading. Mac OS X asks you for you administrator password to install applications for a reason! Only download media and applications from well-known and trusted Web sites, i.e. the developers' own web sites or the Apple App Store. If you think you may have downloaded suspicious files, read the installer packages and make sure they are legit. If you cannot determine if the program you downloaded is infected, do a quick Internet search and see if any other users reported issues after installing a particular program.
3. Use an antivirus program like ClamXav. If you are in the habit of downloading a lot of media and other files, it may be well worth your while to run those files through this AV application.
4. Consider using Mac OS X's built-in Firewalls and other security features.
5. Avoid Peer-to-peer sharing applications. Download torrents (such as the now defunct LimeWire) supplying pirated software, movies etc are hotbeds of potential software issues waiting to happen to your Mac. Everything from changing permissions to downloading trojans and other malicious software can be acquired from using these applications. Similar risks may apply to using Facebook, Twitter, MySpace, YouTube and similar sites which are prone to malicious hacking (see below): http://news.bbc.co.uk/1/hi/technology/8420233.stm
It has been estimated that one in six links posted on Facebook pages are connected to malicious software.http://www.bbc.co.uk/news/technology-12967254
6. Check for security updates from Apple using Software Update and install them!
YOUR PRIVACY ON THE INTERNET and the latest risks to look out for:
There is the potential for having your entire email contact list stolen for use for spamming:
And if you are using iPhone Apps you are also at risk of losing all privacy:
The advent of HTML5 may also be a future threat to internet privacy:
NOTE:Apple's operating systems since Snow Leopard silently update the malware protection built into Mac OS X to protect against a backdoor Trojan Horse that can allow hackers to gain remote control over your treasured iMac or MacBook.
+++++ MORE POTENTIAL ISSUES +++++
PHISHING AND POTENTIAL IDENTITY THEFT:
'Phishing' (also known as 'carding' or 'spoofing') refers to email that attempts to fraudulently acquire personal information from you, such as your account password or credit card information. On the surface, the email may appear to be from a legitimate company or individual, but it's not.
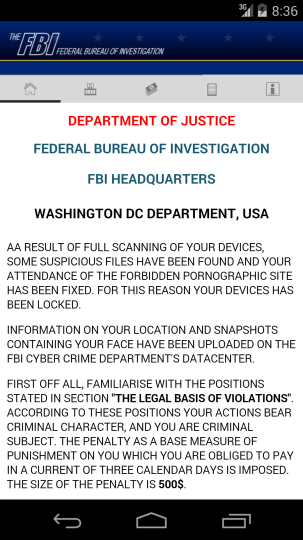
As a general rule, never send credit card information, account passwords, or extensive personal information in an email unless you verify that the recipient is who they claim to be. Many companies have policies that state they will never solicit such information from customers by email, and that includes your bank, credit card company, and Apple.
If you do receive email that you're not sure is valid, here are some tips that can help you determine its legitimacy:
Learn how to identify fraudulent 'phishing' email:
How to report phishing scams to Apple:
via email to: reportphishing@apple.com
If you discover that emails are being received by your entire address list which you didn't send, it is possible that you have been infected by a Botnet. Simply put, a bot – which is short for robot – is an automated computer program that allows outside sources to control computers remotely without the users' knowledge. A botnet is a network of hundreds or thousands of computers infected with botnet malware that communicates covertly with a command-and-control (CnC) server run by a type of cybercriminal called a botmaster. Unbeknownst to the individual users, their computers are linked in a rogue network which the botmaster can utilize for a variety of nefarious purposes.
Detailed information here:
HOW SAFE IS YOUR SMARTPHONE?
Another source of malware, apart from sites like Facebook and Hotmail, is the Android Marketplace: more than 99% of Android phones are potentially leaking data that, if stolen, could be used to get the information they store online.
The data being leaked is typically used to get at web-based services such as Google Calendar.
The open nature of the Android platform is both a boon and a danger, and as Facebook have already discovered it is also a very attractive criminal playground: http://www.bbc.co.uk/news/technology-12633923
Several pieces of malware have also been found on iPhones, however only devices that had been 'jailbroken' to bypass Apple's security were affected. Logitech apple keyboard wireless. The company's process of pre-vetting all new applications is believed to have spared its devices from a major attack.
LAST BUT NOT LEAST: BE GLAD YOU HAVE A MAC!
Some Windows PCs can be infected with viruses during the manufacturing process in the factories - in other words they can actually be purchased with viruses bundled with the operating system! Several new computers have been found carrying malware installed in the factory, suggests a Microsoft study. One virus called Nitol found by Microsoft steals personal details to help criminals plunder online bank accounts. Microsoft won permission from a US court to tackle the network of hijacked PCs made from Nitol-infected computers.

As a general rule, never send credit card information, account passwords, or extensive personal information in an email unless you verify that the recipient is who they claim to be. Many companies have policies that state they will never solicit such information from customers by email, and that includes your bank, credit card company, and Apple.
If you do receive email that you're not sure is valid, here are some tips that can help you determine its legitimacy:
Learn how to identify fraudulent 'phishing' email:
How to report phishing scams to Apple:
via email to: reportphishing@apple.com
If you discover that emails are being received by your entire address list which you didn't send, it is possible that you have been infected by a Botnet. Simply put, a bot – which is short for robot – is an automated computer program that allows outside sources to control computers remotely without the users' knowledge. A botnet is a network of hundreds or thousands of computers infected with botnet malware that communicates covertly with a command-and-control (CnC) server run by a type of cybercriminal called a botmaster. Unbeknownst to the individual users, their computers are linked in a rogue network which the botmaster can utilize for a variety of nefarious purposes.
Detailed information here:
HOW SAFE IS YOUR SMARTPHONE?
Another source of malware, apart from sites like Facebook and Hotmail, is the Android Marketplace: more than 99% of Android phones are potentially leaking data that, if stolen, could be used to get the information they store online.
The data being leaked is typically used to get at web-based services such as Google Calendar.
The open nature of the Android platform is both a boon and a danger, and as Facebook have already discovered it is also a very attractive criminal playground: http://www.bbc.co.uk/news/technology-12633923
Several pieces of malware have also been found on iPhones, however only devices that had been 'jailbroken' to bypass Apple's security were affected. Logitech apple keyboard wireless. The company's process of pre-vetting all new applications is believed to have spared its devices from a major attack.
LAST BUT NOT LEAST: BE GLAD YOU HAVE A MAC!
Some Windows PCs can be infected with viruses during the manufacturing process in the factories - in other words they can actually be purchased with viruses bundled with the operating system! Several new computers have been found carrying malware installed in the factory, suggests a Microsoft study. One virus called Nitol found by Microsoft steals personal details to help criminals plunder online bank accounts. Microsoft won permission from a US court to tackle the network of hijacked PCs made from Nitol-infected computers.
Blueprint software mac free download. This does not happen with Apple computers!
OTHER POTENTIAL THREATS YOU MAY BE UNAWARE OF:
In reality of course, there is no such thing as total internet privacy: US and British intelligence agencies have successfully cracked much of the online encryption relied upon by hundreds of millions of people to protect the privacy of their personal data, online transactions and emails: http://www.theguardian.com/world/2013/sep/05/nsa-gchq-encryption-codes-security
If you have a Facebook account, Facebook is surveilling every single moment you spend there. Moreover, much more importantly, every web page you touch that has a Facebook 'like' button on it which, whether you click the button or not, will report your reading of that page to Facebook.
If the newspaper you read every day has Facebook 'like' buttons or similar services' buttons on those pages, then Facebook or the other service watches you read the newspaper: it knows which stories you read and how long you spent on them.
Every time you tweet a URL, Twitter is shortening the URL for you. But it is also arranging that anybody who clicks on that URL will be monitored by Twitter as they read. You are not only helping people know what's on the web, but also helping Twitter read over everybody's shoulder everything you recommend.
And now ‘smart TVs' are also adding to your loss of privacy: 'Smart TVs' are bringing PC-style spyware and banner ads to the living room, collecting detailed logs of data that include every time the channel is changed and the names of every media file watched. In the case of sets from LG, data is being sent to the factory unencrypted, even after users attempt to turn the data collection off. Source: http://doctorbeet.blogspot.co.uk/2013/11/lg-smart-tvs-logging-usb-filenames-and. html
Since the issue became public it has emerged that Sony's PlayStation also collects data from every Blu-ray disc that is played.
Additional reading:
'Antivirus Software On Your Mac: Yes or No?'
Other malware removal tip and malware removal software sites:
Note: if at all possible before trying to remove malware, do abackupof your data. While you may backup the virus as well, you can usually extract document files themselves which are uninfected from the backup in case the virus removal tool was too thorough. ZIP archives, applications, scpt files and .jar files should be considered infected if you don't know their source:
Malwarebytes for Mac — Mac Antivirus Replacement | Malwarebytes - note removal of this software itself can be done with Download CCleaner | Clean, optimize & tune up your PC, free! (this software also supports removal of system caches, which is NOT recommended).
EasyFind & Find Any File - offer index (no interference from Spotlight) free file searches that allow you to eliminate known malware by file name.
